Experts In Akira Ransomware Decryption & Removal
Akira ransomware attacks are complex and can result in extended downtime. This is generally due to the size of the ransom demands and the logistics involved in ensuring a compliant payment processing.
For most ransomware victims, downtime is the most expensive part of the incident. It can also cause significant reputational damage.
We have worked extensively with Akira ransomware, and we understand very well how the gang operates. This enables us to rapidly resolve attacks and restore files.
How Akira Decryptor works?
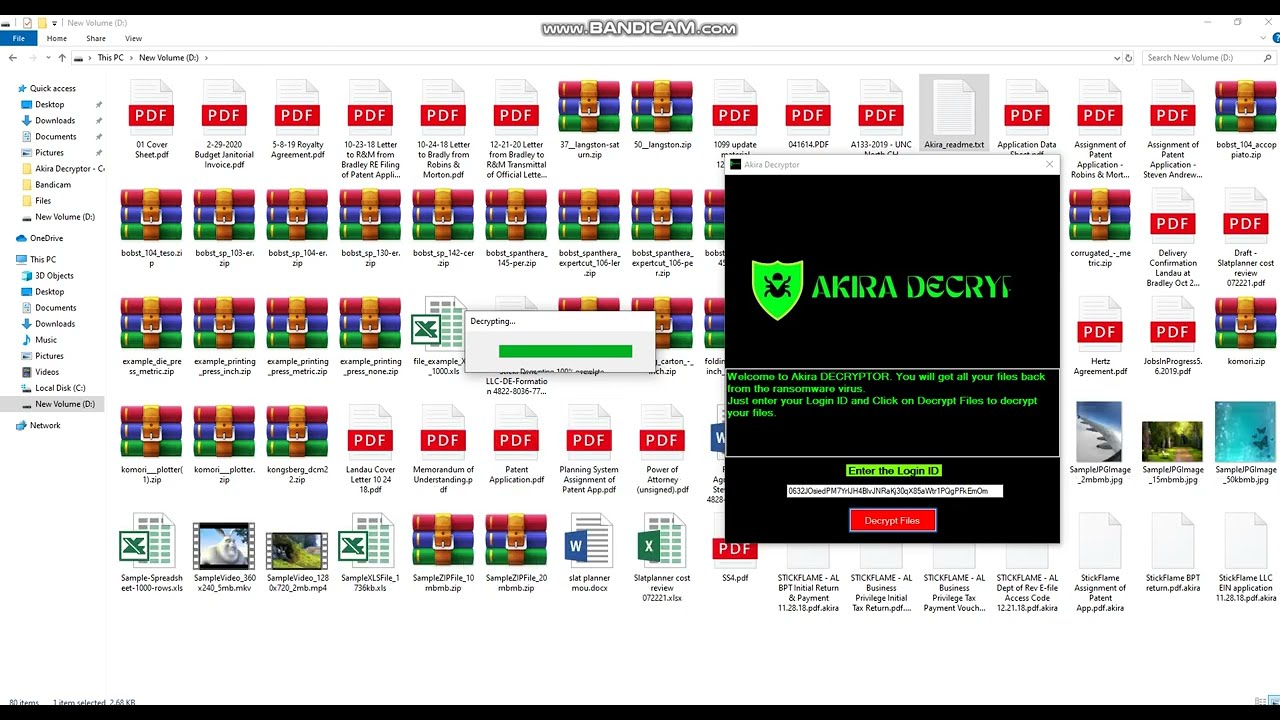
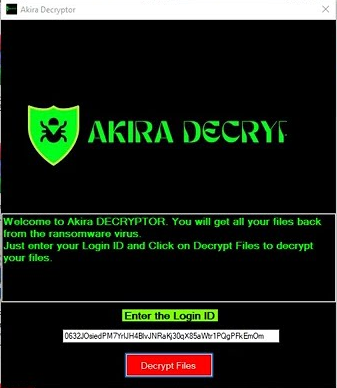
The Akira Decryptor is a highly effective tool for decryption of files affected by Akira Ransomware. It uses online servers to bypass the encryptions of ransomware by connecting via Login ID and then start decrypting the files.
Verify Login ID
The Akira Decryptor asks for the personal id you find in Akira_readme.txt And after putting the ID in the decryptor, it will verify
your login id using an online server.
Bypass Private Key
If your Login ID is valid and verified by the server then the
decryptor will use online server to bypass the private key to
decrypt files.
Decrypt Files
After bypassing the private key of the ransomware using online server. The Akira Decryptor will start
decrypting the files and servers.
Ransomware Recovery Process: How It Works?
Rapid Evaluation
Contact us, submit your case and send us your Login ID for the first rapid evaluation.
DEEP ANALYSIS
We analyze your Login ID to determine the cost associated with recovery.
FAST QUOTE
We send you a quote with information about cost and timing of the recovery.
GUARANTEED RECOVERY
We send you Akira Decryptor via Email and a complete usage guide.
How to know if Akira ransomware infected your system?
Identifying and Addressing Akira Ransomware Infections
If you encounter a situation where all your files are inaccessible, displaying unfamiliar file extensions, or if you receive a ransom note demanding payment for file recovery, you may be dealing with Akira ransomware. First identified in March 2023, Akira ransomware has been targeting organizations with ransom demands ranging from hundreds of thousands to millions of dollars.
Key Indicators of Akira Ransomware Infection
- File Extension Changes: Akira ransomware encrypts files and typically modifies their extensions to “.akira” or other variants. This alteration is a clear sign of encryption.
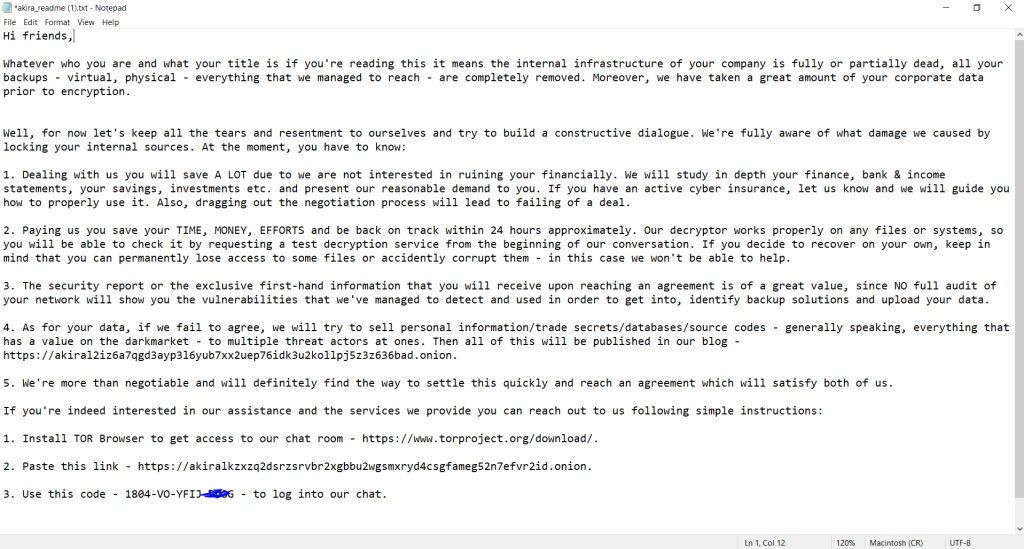
- Ransom Notes: Infected systems will have text files such as “akira_readme.txt” or other variations placed in each encrypted directory. This file usually contains instructions or demands for ransom payment.
- System Performance Issues:
- High CPU Usage: Your CPU may show close to 100% usage, even if no applications are running.
- Slow Performance: The system may experience a noticeable decrease in speed and responsiveness.
- Disk Activity: The hard disk may be continuously reading and writing at full capacity in the background, regardless of active applications.
- Antivirus Malfunctions: Antivirus software might be disabled or fail to function properly during an infection.
Response and Recovery
If you get infected by this ransomware then immedietely turn off your server. Install a good antivirus and scan your system to protect it from furhter damage. Moreover, if you need help regarding the recovery, you can contact us via email or WhatsApp to get the decryptor for Akira ransomware.
Ransom Note by Akira Ransomware
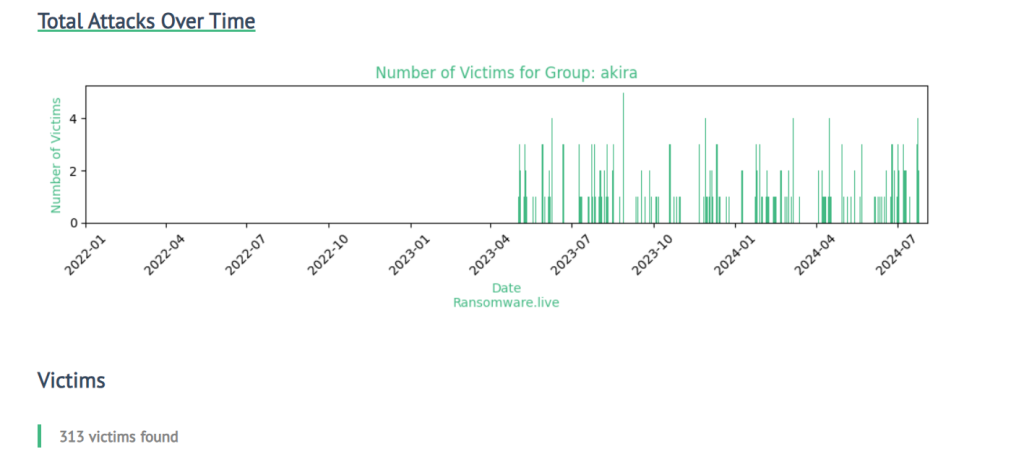
Akira Ransomware Latest Stats:
On average, akira ransomware is attacking more than 20 companies per month. They have attacked more than 300 companies all over the world. Some of the stats are given below:
How to Decrypt ESXI or Linux Servers from Akira Ransomware?
Akira ransomware is targeting Windows as well as Linux based servers such as Vmware esxi servers, hypervisor, CentOS, and others. It encrypts all the VMDK, VHDK, VMX, and other type of files in the server by using special encryptions. Moreover, it also encrypts the Veeam Backups and other bak files too. But, no you don’t need to worry about it as we have decryptor for Akira ransomware that can be used to decrypt Linux servers. We’ll use Akira decryptor.py on Esxi servers to bypass the encryptions and decrypt the files including all data such as VMDK, VHDK, VHDs, and other files. You can watch the video given below to learn about it.
Akira Decryptor FAQS
Email Us
https://wa.me/447405816578
+https://wa.me/447405816578
Some of our Fans
Need Help?
Affected by Ransomware virus need help? Contact us right now to get your data back.