Akira Ransomware is Back Again to Negotiations
Cybersecurity experts have raised alarms as the Akira ransomware group resurfaces with new strategies and a revamped ransom note aimed at pressuring victims into compliance. The group’s latest operations reflect a calculated shift in their approach, leveraging psychological tactics and offering “negotiable” terms to achieve faster settlements.
What’s New in Akira’s Strategy?
The updated ransom note adopts a tone that mixes intimidation with an offer for “constructive dialogue.” The attackers claim they are not interested in financial ruin but rather propose a “reasonable demand” based on the victim’s financial standing, including savings, investments, and cyber insurance coverage.
Key elements of Akira’s new tactics include:
- Financial-Based Demands: The attackers pledge to analyze victims’ financial records before issuing a ransom demand, claiming this approach reduces the financial burden.
- Time-Sensitive Negotiation: Victims are urged to act swiftly, with warnings that delays could lead to data being sold on dark web marketplaces or publicly leaked.
- Test Decryption Offer: The group provides test decryption to assure victims of their decryptor’s effectiveness, aiming to build trust and encourage payment.
- Data Exploitation Threat: If negotiations fail, the attackers threaten to sell or leak exfiltrated data, including sensitive trade secrets and personal information.
- Exclusive Security Report: The group promises to provide a report detailing the vulnerabilities they exploited, positioning it as a bonus for compliance.
The Ransom Note
The new ransom note begins with a casual but ominous greeting:
Hi friends,
Whatever who you are and what your title is if you’re reading this it means the internal infrastructure of your company is fully or partially dead, all your backups – virtual, physical – everything that we managed to reach – are completely removed. Moreover, we have taken a great amount of your corporate data prior to encryption.
Well, for now let’s keep all the tears and resentment to ourselves and try to build a constructive dialogue. We’re fully aware of what damage we caused by locking your internal sources. At the moment, you have to know:
- Dealing with us you will save A LOT due to we are not interested in ruining your financially. We will study in depth your finance, bank & income statements, your savings, investments etc. and present our reasonable demand to you. If you have an active cyber insurance, let us know and we will guide you how to properly use it. Also, dragging out the negotiation process will lead to failing of a deal.
- Paying us you save your TIME, MONEY, EFFORTS and be back on track within 24 hours approximately. Our decryptor works properly on any files or systems, so you will be able to check it by requesting a test decryption service from the beginning of our conversation. If you decide to recover on your own, keep in mind that you can permanently lose access to some files or accidently corrupt them – in this case we won’t be able to help.
- The security report or the exclusive first-hand information that you will receive upon reaching an agreement is of a great value, since NO full audit of your network will show you the vulnerabilities that we’ve managed to detect and used in order to get into, identify backup solutions and upload your data.
- As for your data, if we fail to agree, we will try to sell personal information/trade secrets/databases/source codes – generally speaking, everything that has a value on the darkmarket – to multiple threat actors at ones. Then all of this will be published in our blog – [Snip].
- We’re more than negotiable and will definitely find the way to settle this quickly and reach an agreement which will satisfy both of us.
If you’re indeed interested in our assistance and the services we provide you can reach out to us following simple instructions:
- Install TOR Browser to get access to our chat room – https://www.torproject.org/download/.
- Paste this link – VICTIM_CHAT_URL
- Use this code – [snip]- to log into our chat.
Keep in mind that the faster you will get in touch, the less damage we cause.”
The note outlines the group’s demands, the potential consequences of non-compliance, and instructions for contacting them via a TOR-based chat room using a unique login code.
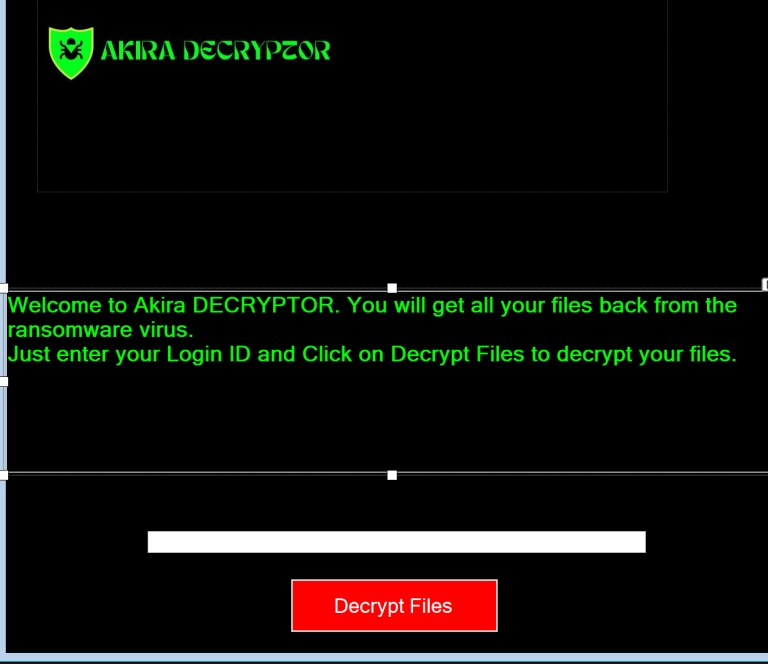
Akira Ransomware Decryption Tool Now Available
If your organization has been impacted by Akira ransomware, you don’t need to succumb to their demands. A free decryption tool is now available to help victims recover their encrypted files without paying the ransom.
How to Use the Akira Decryption Tool
- Download the Decryption Tool: Access the decryption tool from a trusted cybersecurity source.
- Isolate the Infected Systems: Disconnect infected devices from the network to prevent further spread.
- Run the Tool: Follow the provided instructions to decrypt the affected files safely.
- Restore from Backup (If Needed): If some files remain inaccessible, use your latest backups for full recovery.
Where to Get the Tool
You can download the Akira ransomware decryption tool from [Insert Trusted Cybersecurity Provider’s Name/Link Here]. Make sure to verify the authenticity of the tool and seek expert guidance if needed.
Protect Yourself from Future Attacks
To prevent falling victim to Akira or other ransomware attacks in the future, organizations should:
- Implement robust backup strategies with offline storage.
- Deploy advanced endpoint detection and response (EDR) systems.
- Educate employees on phishing and social engineering tactics.
- Conduct regular vulnerability assessments and patch management.
- Develop a comprehensive incident response plan for ransomware scenarios.
Conclusion
Akira ransomware’s resurgence highlights the growing sophistication of cybercriminal operations. With a free decryption tool now available, victims can regain access to their data without engaging in negotiations. However, the best defense against ransomware remains prevention through strong cybersecurity measures and proactive monitoring.
For assistance or to purchase the decryption tool, contact us via WhatsApp. Protect your organization before it’s too late.