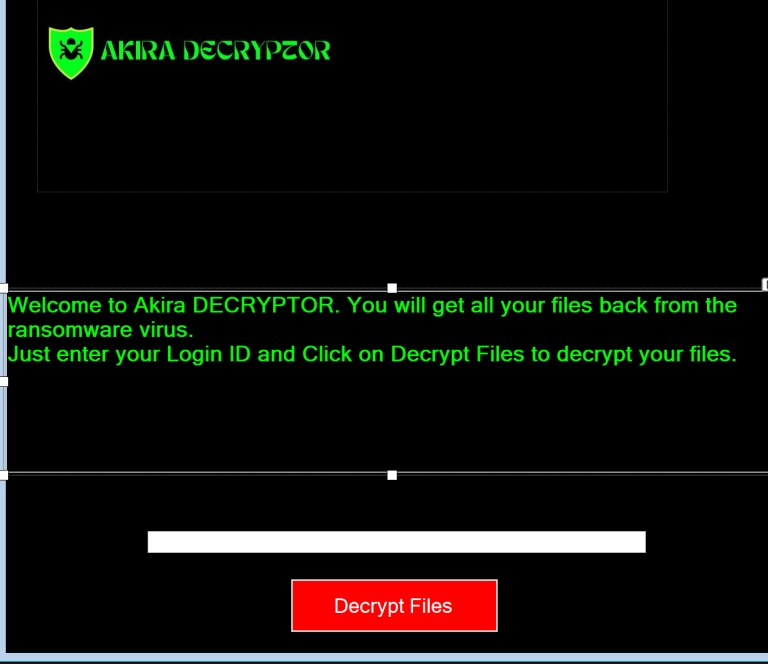
Decrypting Akira Ransomware with Brute-Force in 2025
Security researcher Yohanes Nugroho has released a decryptor for the Linux variant of Akira ransomware, which utilizes GPU power to retrieve the decryption key and unlock files for free. Nugroho developed the decryptor after being asked for help from a friend, deeming the encrypted system solvable within a week based on how Akira generates encryption…