How to Recover ESXI Servers from Akira Ransomware?
Akira ransomware has emerged as a significant threat to VMware’s ESXi hypervisors, targeting virtualized environments by encrypting critical data and demanding ransoms in cryptocurrency. If your ESXi servers have fallen victim to Akira ransomware, decrypting your encrypted virtual machines is paramount for restoring operations and minimizing disruptions. This comprehensive guide will walk you through the process of using the Akira decryptor to recover your data.
Understanding Akira Ransomware and Its Impact
Akira ransomware specifically targets VMware ESXi servers, leveraging vulnerabilities in the hypervisor to encrypt virtual machines and their associated files. The ransomware uses advanced encryption algorithms, such as RSA or AES, rendering the encrypted machines inaccessible until a ransom is paid. Typically, after encryption, attackers demand payment in cryptocurrency and threaten to delete decryption keys if the ransom is not settled within a specified timeframe.
Initial Steps for Decryption
Before using any decryption tools, follow these crucial initial steps to ensure a successful recovery process:
- Isolate Affected Servers: Immediately isolate the compromised ESXi servers from the network to prevent further encryption and limit the spread of the ransomware.
- Assess the Attack: Evaluate the extent of the encryption to understand which virtual machines and files have been affected. This will help in the recovery process and in deciding the best course of action.
- Consult with Experts: Engage with our professionals to assess the situation. They can provide insights into the attack, verify the encryption method used, and recommend suitable decryption tools.
Using the Akira Decryptor for ESXI
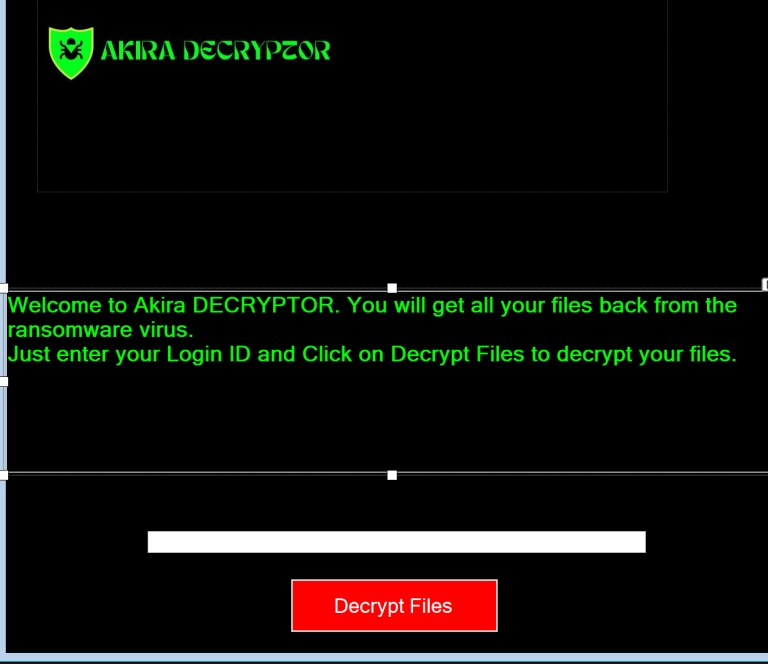
The Akira decryptor is a specialized tool designed to reverse the encryption performed by the ransomware. Here’s a step-by-step guide on how to use it:
- Purchase the Akira Decryptor:
- Obtain the Akira decryptor from our company by contacting via Email or WhatsApp. The decryptor will cost you some money based on the number of data.
- Prepare Your Environment:
- Before running the decryptor, ensure that you have a secure and isolated environment to prevent any accidental spread of the ransomware.
- Backup all encrypted files, if possible, to avoid any data loss during the decryption process.
- Install the Decryptor:
- Follow the installation instructions provided with the Akira decryptor. This typically involves executing an installation file and configuring the decryptor according to the instructions.
- Run the Decryptor:
- Launch the decryptor tool and provide it with the necessary information, such as the encrypted files’ location and any additional data it requires.
- The decryptor will analyze the encrypted files and begin the decryption process. This can take some time, depending on the volume of data and the complexity of the encryption.
- Verify Decryption:
- Once the decryption process is complete, verify that the virtual machines and files have been successfully decrypted and are accessible.
- Test critical systems to ensure that all functionalities are restored and that there are no lingering issues.
You can watch the video given below for futher information regarding esxi recovery from Akira ransomware.
Post-Recovery Actions
After successfully decrypting your data, it’s essential to take steps to strengthen your security and prevent future attacks:
- Update and Patch Systems:
- Apply the latest security patches to your ESXi hypervisors and associated software to close known vulnerabilities that the ransomware may have exploited.
- Implement Robust Security Measures:
- Strengthen access controls and authentication mechanisms to prevent unauthorized access to your ESXi environment.
- Consider enhancing network segmentation to limit the impact of any future ransomware attacks.
- Review and Improve Backup Procedures:
- Ensure that you have regular, encrypted backups of all critical data stored in secure locations. Regularly test your backup and recovery procedures to ensure their effectiveness.
- Conduct a Security Audit:
- Perform a thorough security audit to identify any potential weaknesses in your infrastructure and address them promptly.
- Educate and Train Staff:
- Provide cybersecurity training for your staff to recognize phishing attempts and other common attack vectors that could lead to ransomware infections.
Conclusion
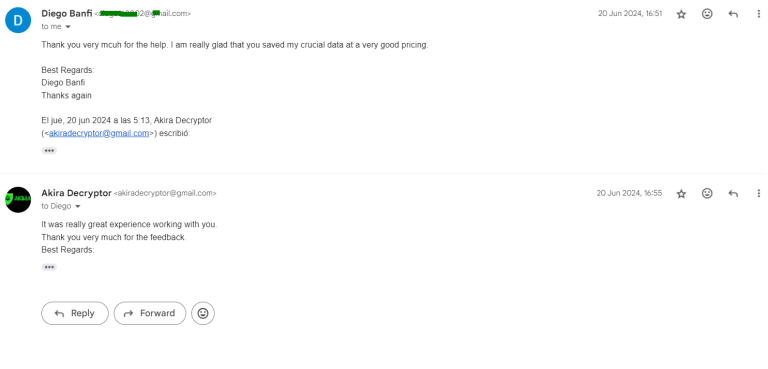
Decrypting Akira ransomware from ESXi servers requires careful planning and execution. By following the steps outlined above and utilizing the Akira decryptor, you can recover your encrypted data and restore normal operations.
However, decryption is just one part of the recovery process. Implementing strong security measures and maintaining robust backup procedures are crucial for protecting your virtualized infrastructure against future threats. Always stay vigilant and proactive in your cybersecurity efforts to safeguard your systems from ransomware and other malicious attacks.